Zero Trust in 2025 — Momentum, Barriers, and How to Scale
10/18/20252 min read
Zero Trust is strategic — but scaling is hard. Learn practical steps to avoid abandonment and succeed in 2025.
Introduction
If the term Zero Trust still feels a bit buzz-wordy or abstract, you’re not alone. The concept of “never trust, always verify” has been around for years — but in 2025, it’s no longer optional. The hard part? Making it real, making it scale, and tying it to business outcomes.
Let’s chat about where Zero Trust stands now, what’s helping and what’s holding organisations back — and how you can get traction.
Trend explanation & data-driven insights
According to Gartner, Zero Trust is one of the top cybersecurity trends for 2025. But here’s the kicker: many organisations may abandon their efforts if they stay siloed, manual or tactical. Gartner+1
Key friction points: too many separate tools, lack of identity-device-network integration, poor visibility across cloud/on-prem, and lack of clear business KPIs.
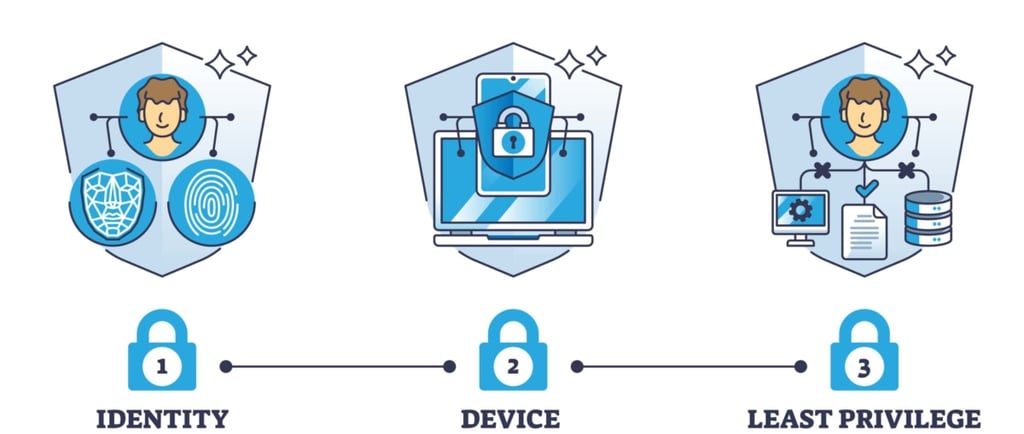
A big insight: success depends on combining identity, device posture, network segmentation, cloud access and automation — not just deploying MFA or micro-segmentation and calling it done.
Real-world examples / case studies
An enterprise rolled out MFA and micro-segmentation but stalled because identity analytics and device posture were missing — they couldn’t measure friction vs. risk and the project lost momentum.
Another organisation adopted a vendor platform that bundled identity, device posture and SASE-style network access, then tracked metrics like “time to revoke access after compromise” and saw meaningful improvement in months.
Best practices & recommendations
Begin with identity & device posture: make sure each login has strong context (who, what device, where, how) and enforce required posture before granting access.
Automate policy lifecycle: avoid manual rule-creation that becomes unmanageable. Use policy orchestration, dynamic segmentation and automated policy-decommissioning when services change.
Align to business outcomes: pick KPIs such as reduction in “privileged access events”, “time to detect compromised account”, or “users with excessive privileges” — not just “we enabled MFA”.
Plan for cloud + hybrid: Zero Trust in 2025 must span on-prem, cloud, SaaS and remote users with consistent policy and telemetry.
Monitor for drift and enforce continuous validation: Zero Trust isn’t a one-time project — it’s an ongoing state of verification, validation and adaptation.
Conclusion & future outlook
Zero Trust isn’t going away — it’s becoming a foundational part of enterprise security in 2025 and beyond. But success lies not in launching a pilot, but in scaling it, governing it, automating it and linking it to business value. Organisations that treat Zero Trust as a journey (not a checkbox) will differentiate themselves. Over the next few years expect more consolidation of Zero Trust + SASE + cloud identity platforms and possibly standards around “Zero Trust maturity”.
It’s time to get moving — the momentum is here.
