Ransomware-as-a-Service & the Professionalisation of Extortion
10/18/20252 min read
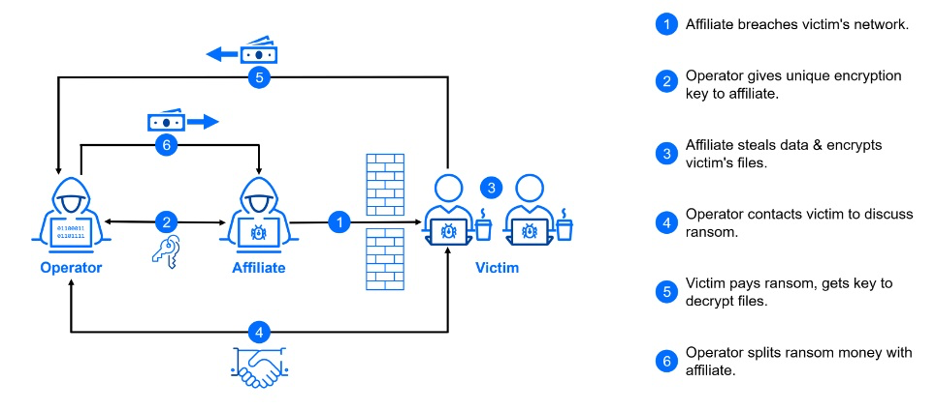
Ransomware isn’t just malware anymore — it’s a service-driven, affiliate-based business. See how to defend and respond in 2025.
Introduction
Alright — we all know about classic ransomware: you’re locked out, bad actor demands payment. But what many miss is the evolution: ransomware has become a fully-fledged industry model known as Ransomware-as-a-Service (RaaS). There are affiliates, service desks, legal-style negotiation teams, cloud-based C2 infrastructure, double-extortion tactics and more. This blog walks you through how ransomware has matured, what patterns you should watch, and how to build response posture accordingly.
Trend explanation & data-driven insights
The Cybersecurity & Infrastructure Security Agency (CISA) and other national authorities continue to flag new ransomware-families and affiliate-based models where the core developers supply the kit and affiliates pick the targets.
Incident-response teams (such as from Palo Alto’s Unit 42) report that ransom operations increasingly use cloud services for command-and-control and exfiltration, making detection harder and response more urgent. CrowdStrike+1
The complexity is increasing: impacts aren’t just encryption—they’re data theft, leak threats, reputational damage and regulatory costs.
Real-world examples / case studies
The group known as Interlock (among others) is cited in security research as an affiliate platform targeting multiple OSes (Windows, Linux, ESXi), using legitimate cloud storage for exfiltration and a built-in negotiation desk.
Many organisations that were hit report that their backup strategy saved them from paying ransom—but they still faced huge costs from downtime, leak remediation and brand damage.
Best practices & recommendations
Backups & restores are non-negotiable: Ensure immutable backups, offline copies, frequent restore testing and segmentation of backup networks.
Patch and harden remote-access & RMM tools: Many ransomware campaigns start with exposed remote tools or compromised credentials. Map and monitor.
Enforce phishing-resistant MFA and monitor internal lateral movement: Prevent credential abuse and detect early signs of break-out.
Have an incident-response plan: Define roles, simulate attacks, have cyber-insurance clarity and legal counsel in place. Speaking to experts early makes a difference.
Limit data access and exfiltration readiness: Apply data-loss-prevention controls, monitor large outbound transfers, and keep an eye on unusual cloud/FTP flows.
Conclusion & future outlook
Ransomware in 2025 is not just a “bitlocker + demand” event—it’s a business ecosystem that demands a strategic, enterprise-wide response. Organisations that treat it as just “IT issue” are at risk of being blindsided. Over the next few years expect more regulation around ransom payments, more emphasis on disclosure and more pressure on supply-chain security (because affiliates target weak links). The good news? With strong posture, you can turn the tables and reduce your exposure. Are you ready?
