Developing strategies for effective incident management and recovery
Zaheer Ikbal
10/29/2025
Navigating the Storm: Strategies for modern incident response and recovery
In the dynamic digital world, the question isn't if your organization will face a cyber incident, but when. A well-defined incident response plan is no longer a luxury; it's a necessity for safeguarding data, maintaining business continuity, and preserving your reputation. This blog post will explore strategies for effective incident management and recovery, focusing on the latest threats and emerging technologies that are reshaping network security.
The new reality: Faster, stealthier attacks
The cybersecurity landscape is evolving at a breakneck pace, driven by sophisticated and automated techniques that exploit emerging technologies. Here are some of the critical threats challenging traditional defenses in 2025:
AI-powered attacks: Malicious AI tools are creating hyper-realistic phishing emails and deepfake social engineering, making traditional training less effective.
Professionalized ransomware: Attackers now use a "double extortion" model, stealing sensitive data before encrypting it. Some groups even employ "triple extortion," adding DDoS attacks to pressure victims.
Cloud and identity compromise: With the shift to cloud-first environments, identity has become the new perimeter. The abuse of compromised credentials is a leading cause of breaches, compounded by cloud misconfigurations.
Supply chain vulnerabilities: Attackers are targeting trusted third-party vendors and open-source libraries to launch widespread attacks, exploiting the inherent trust within the supply chain.
Living off the land (LotL): Many hands-on-keyboard intrusions are now malware-free, using legitimate system tools to evade detection by legacy security products.
Your resilient defense: A proactive incident response strategy
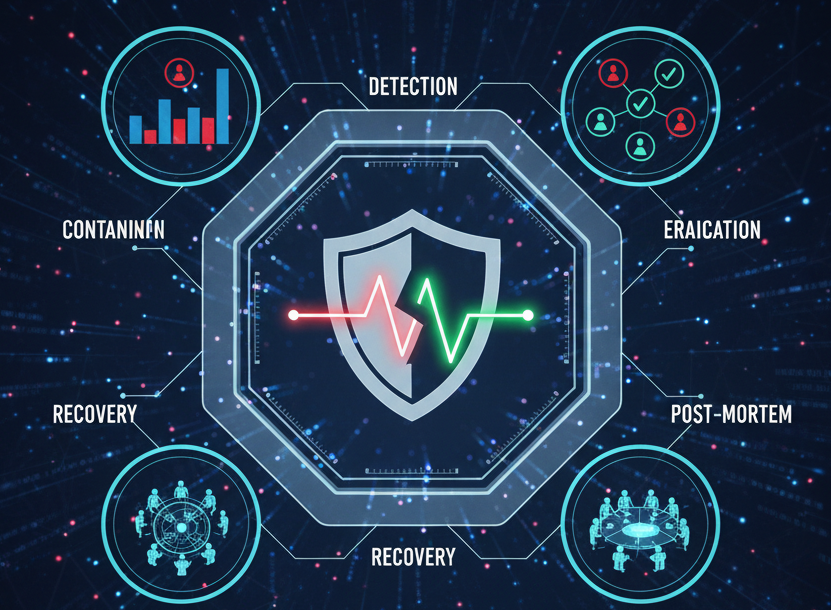
To combat these advanced threats, your incident response (IR) strategy must move beyond a reactive stance toward a model of proactive resilience. A robust IR plan follows a clear lifecycle: preparation, detection and analysis, containment, eradication, recovery, and post-incident lessons learned.
Phase 1: Preparation
This is the most critical stage. It involves laying the groundwork for a swift and organized response.
Develop a customized plan: A generic template won't cut it. Tailor your IR plan to your organization's specific risks, business objectives, and technology stack.
Create incident playbooks: Build specific, detailed action plans for different types of threats, such as ransomware, phishing, or DDoS attacks. These playbooks act as a battle guide during a high-pressure situation.
Assemble your team: Identify key stakeholders from IT, security, management, legal, and communications. Clearly define roles, responsibilities, and escalation paths.
Conduct regular training: Your IR plan is only as effective as the people who execute it. Run regular tabletop exercises and realistic simulations (red team exercises) to test your team's readiness and identify gaps.
Phase 2: Detection and analysis
Leverage advanced tools and techniques to identify potential breaches rapidly.
Implement AI-powered detection: Invest in security solutions that use AI and machine learning (ML) to analyze network traffic and user behavior in real-time. These tools can detect subtle anomalies that signal a LotL attack.
Enhance endpoint visibility: Deploy Endpoint Detection and Response (EDR) or Extended Detection and Response (XDR) solutions across all endpoints and cloud workloads. These solutions provide deep visibility into system activities, which is critical for identifying malware-free attacks.
Phase 3: Containment and eradication
Isolate affected systems to prevent the incident from spreading and eliminate the threat.
Embrace Zero Trust: The principle of "never trust, always verify" is a powerful containment tool. Use network microsegmentation to create isolated enclaves, restricting an attacker's ability to move laterally across the network.
Isolate and block: Use your security tools to quickly disconnect affected devices, block malicious IP addresses, and quarantine threats. For ransomware, this includes isolating systems to prevent encryption from spreading.
Identify the root cause: Forensic investigation is crucial to understanding how the attack occurred so you can eliminate the underlying vulnerability.
Phase 4: Recovery
Restore systems and data securely to return to normal operations.
Utilize immutable backups: This is your most critical defense against ransomware. Maintain multiple copies of critical data, with at least one stored offline in an immutable format that cannot be altered or deleted. Test your restoration process regularly.
Restore and validate: Restore systems from clean, verified backups and perform thorough testing to ensure normal functionality before bringing them back online.
Phase 5: Post-incident analysis
Turn a crisis into an opportunity for growth and improvement.
Hold a blameless post-mortem: Analyze what worked, what didn't, and why, without assigning blame.
Create an action plan: Document lessons learned and assign tasks to address identified weaknesses. This could involve updating security controls, implementing new technologies, or conducting additional training.
Track metrics: Measure your response time and other key performance indicators to assess improvements over time.
Emerging technologies for enhanced incident response
Looking ahead, several emerging technologies will provide new tools for building a more resilient defense.
Quantum-resistant cryptography: As quantum computing develops, it threatens traditional encryption methods. Organizations should begin adopting post-quantum cryptography (PQC) now to protect against future decryption threats.
Blockchain for data integrity: While known for cryptocurrencies, blockchain's immutable ledger can be used to ensure data integrity. It provides a secure way to store critical data, making unauthorized changes immediately detectable.
Behavioral biometrics: This technology analyzes unique user behaviors, such as typing patterns and mouse movements, to continuously verify a user's identity. It provides a dynamic layer of security that is much harder for attackers to spoof.
Digital twins for simulation: A cyber-twin is a virtual representation of your network and systems. It can be used to run simulations of potential cyberattacks and test your defenses in a safe environment.
Final thoughts
In the face of an increasingly sophisticated threat landscape, a modern incident response strategy is your best defense. By adopting a proactive mindset, leveraging advanced technologies, and focusing on continuous improvement, your organization can move from simply reacting to threats to building a truly resilient security posture. The time to prepare is now, before the next incident hits.
