Designing Robust Network Security Frameworks & Protocols: A Friendly Dive into the Future
10/29/2025


Designing Robust Network Security Frameworks & Protocols: A Friendly Dive into the Future
In today’s world, network security is no longer just a technical concern — it's mission critical. As organizations expand, adopt cloud, edge, IoT, and AI, the attack surface grows exponentially. Building a “robust” framework means staying a step ahead — combining proven principles, modern tools, and forward-looking thinking. In this post, I’ll walk you through how to design strong network security frameworks and protocols: what to include, what’s changing, and what tomorrow may bring — all in an approachable way.
1. Why Network Security Frameworks Matter
Imagine trying to secure a city with no roads map, no rules for access, and no incident response plan. Chaos, right? A network security framework is like the city’s blueprint: it defines roles, zones, rules, and how to respond when trouble strikes.
A solid framework helps you:
Align security with business goals (so you don’t over-secure or under-secure)
Ensure consistency across teams, geographies, technologies
Manage risk — you can see where your weak spots are
Adapt and evolve — update parts without breaking everything
Ensure compliance and auditability
In 2025, frameworks also need to support crypto agility (being ready to swap cryptographic methods) and identity-first thinking, since identity is increasingly the new perimeter. (IBM)
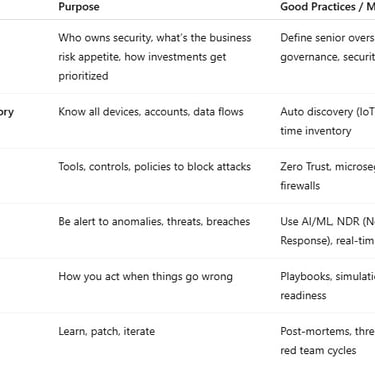
2. Key Building Blocks of a Good Framework
While frameworks differ, most successful ones include these pillars:
A classic example is NIST’s Cybersecurity Framework (CSF), which structures around Identify – Protect – Detect – Respond – Recover. That framework is getting updated (NIST CSF 2.0) to include newer governance and manufacturing profiles. (NIST)
3. Essential Network Security Protocols to Know
Protocols are the languages and guardrails of communication. Here's a digest of key ones you should be familiar with in 2025:
TLS / SSL – Encrypts web traffic (HTTPS) to protect confidentiality and integrity (Cato Networks)
IPsec / IKEv2 – For VPNs and secure site-to-site tunnels (Cato Networks)
DNS over HTTPS (DoH) – Encrypts DNS lookups, preventing domain eavesdropping or spoofing (Uninets)
EAP (Extensible Authentication Protocol) / EAP-NOOB – For network access control, especially in IoT scenarios with no pre-existing credentials (Wikipedia)
802.1X (Port-based Network Access Control) – Enforces that only authenticated devices can join a LAN segment (Pyramid Solutions)
Post-quantum / quantum-resistant cryptography – Emerging protocols designed to be safe even when quantum computers arrive (CableLabs)
When you combine protocols with policies (e.g. what ciphers are allowed, which TLS versions, fallback rules), you define the “rules of engagement” for communication.
4. What’s New & Emerging in 2025
This is where things get exciting — and a little scary.
Adaptive / Intelligent Security
Researchers are already building dynamically retrainable firewalls — firewalls driven by machine learning that can evolve rules in real time based on traffic patterns. (arXiv)
This means less manual tweaking and more proactive defense.
AI & ML Everywhere
AI is now a double-edged sword. Defense uses AI/ML for anomaly detection, threat prediction, and automated triage. But attackers are also using generative and agentic AI to craft more convincing phishing, bypass controls, or launch “smart” attacks. (SentinelOne)
Your framework must assume AI-based threats (and plan countermeasures).
Zero Trust & SASE
Zero Trust (never trust, always verify) continues to replace traditional “castle-and-moat” models. Meanwhile, SASE (Secure Access Service Edge) merges networking (WAN) and security (firewalls, CASB) in the cloud — great for hybrid work. (Pomeroy)
Quantum & Post-Quantum Cryptography
Quantum computers, once mature, could break many classical cryptographic schemes. The industry is now standardizing post-quantum algorithms and pushing crypto agility (ability to swap algorithms fast). (IBM)
Notably, Cloudflare will integrate post-quantum cryptography into its Zero Trust stack by mid-2025. (barrons.com)
Confidential Computing
Even if data is encrypted at rest or in transit, it’s vulnerable when “in use” (processing). Confidential computing protects data in use using hardware-based secure enclaves (Trusted Execution Environments). (Wikipedia)
🛰️ Quantum Key Distribution (QKD) & Quantum-Secure Links
Quantum communication is making strides. For instance, scientists have successfully sent quantum-encrypted messages over a 254 km telecom network — a major step toward real-world quantum-secure communications. (Financial Times)
This could become part of future network protocols in high-security domains.
5. How to Design a Framework That Lasts (Instead of Widely Fails)
Here are practical tips, pitfalls, and patterns:
Start with Risks & Use Cases
Map out what you're protecting (data, services, processes), who uses them, and from which threats (insider/pre-auth, external, supply chain, etc.). Don’t start with tools — start with risk.
Use Layered Defenses
Never rely on a single control. Combine network segmentation, microsegmentation, endpoint security, identity, encryption, anomaly detection, and behavior analytics.
Embrace Identity as the New Perimeter
Users, devices, services — always verify before granting any access. That includes continuous evaluation, not just one-time login.
Build for Crypto Agility
Don’t bake in fixed cryptographic choices. Use abstraction layers so you can upgrade algorithms (e.g. from RSA to PQC) when needed.
Simulate & Test
Run red team / blue team exercises. Test failure cases, how systems respond when one control is down. Validate recovery.
Monitor & Feed Back
You need real-time telemetry, logging, correlation (SIEM), and feedback loops. Use threat intelligence to update rules.
Governance & Collaboration
Ensure alignment across security, network, dev teams. Define roles, accountability, review cycles.
Plan for Change
Technology moves fast. Build modular architecture so upgrades (e.g. swapping encryption, adding zero trust modules) don’t require complete rebuilds.
6. Sample Architecture Sketch: Putting It All Together
Here’s a simplified flow of how a modern network security framework might look:
User / device connects → must authenticate via identity system (MFA, certificate)
Access broker (zero trust gateway / SASE) checks policy (role, device posture, behavior)
Traffic moves through microsegmented zones — e.g. user zone, app zone, database zone
Encryption in transit using TLS or IPsec, with future-forward PQC support
Behavioral / anomaly engine inspects traffic (either inline or out-of-band)
If threat detected, response module kicks in (block, alert, isolate)
Audit & logs feed security analytics / feedback loop
Recovery / fallback plans (e.g. alternate paths, failover, forensic fallback)
Each zone has its policies, encryption, segmentation, detection logic, and tools — yet they must all integrate and share visibility.
7. What to Watch Out For & Common Pitfalls
Relying on “security by obscurity” — hiding systems is not enough
Overly complex policies that no one understands
Skipping telemetry / observability — “you can’t defend what you can’t see”
Ignoring insider threats or compromised credentials
Treating AI only as “nice-to-have” rather than essential defense
Not planning for cryptographic change (i.e. being stuck when quantum hits)
Siloed teams — network, security, development should collaborate
8. The Road Ahead: What to Expect in the Next 5 Years
More agentic AI adversaries — AI systems can launch and coordinate attacks autonomously
Widespread adoption of post-quantum cryptography and hybrid crypto systems
Greater use of confidential computing in distributed/edge environments
Quantum-secure links / QKD becoming parts of critical infrastructure
Adaptive security meshes — real-time reconfiguration of security controls based on context
9. Final Thoughts
Designing robust network security frameworks and protocols is not a one-time exercise — it’s a continuous journey. As threats evolve, so must your architecture. But the guiding principles remain: clarity, identity-first, layered defense, adaptability, and constant feedback.